100+ LUẬN VĂN THẠC SĨ Công Nghệ Thông Tin
Effect of cooperation on players’ immersion and enjoyment - Effect of cooperation on players' immersion and enjoyment
TABLE OF CONTENTS ABSTRACT ……………………………………………………………………………………………………….. iii ACKNOWLEDGMENTS ……………………………………………………………………………………. iv LIST OF ILLUSTRATIONS ……………………………………………………………………………….. vii LIST OF TABLES …………………………………………………………………………………………….. viii SECTION 1. INTRODUCTION ………………………………………………………………………………………… 1 2. LITERATURE REVIEW ………………………………………………………………………………. 3 2.1. COOPERATIVE PLAY AND ENJOYMENT …………………………………………… 3 2.2. PRIOR RESEARCH ON IMMERSION …………………………………………………… 4 3. THEORETICAL...
Using eye-tracking to understand user behavior in deception detection system interaction - Using eye-tracking to understand user behavior in deception detection system interaction
TABLE OF CONTENTS ABSTRACT ……………………………………………………………………………………………………….. iii ACKNOWLEDGMENTS ……………………………………………………………………………………. iv LIST OF FIGURES …………………………………………………………………………………………….. vi LIST OF TABLES ……………………………………………………………………………………………… vii SECTION 1. INTRODUCTION ………………………………………………………………………………………. 1 2. LITERATURE REVIEW …………………………………………………………………………….. 3 3. RESEARCH METHODOLOGY ………………………………………………………………….. 8 3.1. EXPERIMENTAL DESIGN …………………………………………………………….. 8 3.2. EXPERIMENT PROCEDURES ……………………………………………………….. 8 4....
Impact of framing and priming on users’ behavior in cybersecurity - Impact of framing and priming on users' behavior in cybersecurity
TABLE OF CONTENTS ABSTRACT ……………………………………………………………………………………………………….. iii ACKNOWLEDGMENTS ……………………………………………………………………………………. iv LIST OF ILLUSTRATIONS ………………………………………………………………………………. viii LIST OF TABLES ………………………………………………………………………………………………. ix SECTION 1. INTRODUCTION ……………………………………………………………………………………….1 2. LITERATURE REVIEW ……………………………………………………………………………..3 2.1. USERS’ BEHAVIOR IN CYBERSECURITY …………………………………………3 2.2. LITERATURE REVIEW ON MESSAGE FRAMING ……………………………..4 2.3. LITERATURE REVIEW ON PRIMING...
Sentiment analytics – Lexicons construction and analysis - Sentiment analytics - Lexicons construction and analysis
TABLE OF CONTENTS ABSTRACT ……………………………………………………………………………………………………….. iii ACKNOWLEDGMENTS ……………………………………………………………………………………. iv LIST OF ILLUSTRATIONS ………………………………………………………………………………… vi LIST OF TABLES ……………………………………………………………………………………………… vii NOMENCLATURE ………………………………………………………………………………………….. viii SECTION 1. INTRODUCTION ………………………………………………………………………………………… 1 1.1. SENTIMENT ANALYSIS …………………………………………………………………….. 1 1.2. SENTIMENT LEXICON ……………………………………………………………………….. 1 1.3. DESIGN SCIENCE ……………………………………………………………………………….. 2 2. LITERATURE REVIEW...
Neural correlates of flow, boredom, and anxiety in gaming – An electroencephalogram study - Neural correlates of flow, boredom, and anxiety in gaming - An electroencephalogram study
TABLE OF CONTENTS ABSTRACT ……………………………………………………………………………………………………….. iii ACKNOWLEDGMENTS ……………………………………………………………………………………. iv LIST OF ILLUSTRATIONS ………………………………………………………………………………. viii LIST OF TABLES ……………………………………………………………………………………………….. x SECTION 1. INTRODUCTION ………………………………………………………………………………………… 1 2. LITERATURE REVIEW ………………………………………………………………………………. 5 2.1. FLOW STATE AS OPTIMAL EXPERIENCE …………………………………………. 5 2.2. DEFINITION AND CORRELATES OF BOREDOM STATE ………………….....
Impact of probable and guaranteed monetary value on cybersecurity behavior of users - Impact of probable and guaranteed monetary value on cybersecurity behavior of users
TABLE OF CONTENTS ABSTRACT ……………………………………………………………………………………………………….. iii ACKNOWLEDGMENTS ……………………………………………………………………………………. iv LIST OF ILLUSTRATIONS ………………………………………………………………………………. viii LIST OF TABLES ………………………………………………………………………………………………. ix SECTION 1. INTRODUCTION ……………………………………………………………………………………….1 2. LITERATURE REVIEW ……………………………………………………………………………..3 2.1. EFFECT OF USER BEHAVIOR ON INFORMATION SECURITY ………….3 2.2. MESSAGE FRAMING …………………………………………………………………………8 3. THEORETICAL FOUNDATION AND HYPOTHESES...
Classification of EEG signals of user states in gaming using machine learning - Classification of EEG signals of user states in gaming using machine learning
TABLE OF CONTENTS ABSTRACT ………………………………………………………………………………………………………………… iii ACKNOWLEDGMENTS …………………………………………………………………………………………… iv LIST OF ILLUSTRATIONS. …………………………………………………………………………………….. vii LIST OF TABLES…………………………………………………………………………….viii SECTION 1. INTRODUCTION ………………………………………………………………………………………………… 1 2. LITERATURE REVIEW ……………………………………………………………………………………… 3 2.1. USER STATES ……………………………………………………………………………………………… 3 2.2. ELECTROENCEPHALOGRAM (EEG)…………………………………………..4 2.3. RELATED WORK …………………………………………………………………..5 3. RESEARCH METHODOLOGY ………………………………………………………………….. 12 3.1....
Impact of framing and base size of computer security risk information on user behavior - Impact of framing and base size of computer security risk information on user behavior
TABLE OF CONTENTS ABSTRACT ……………………………………………………………………………………………………….. iii ACKNOWLEDGMENTS ……………………………………………………………………………………. iv LIST OF ILLUSTRATIONS ………………………………………………………………………………. viii LIST OF TABLES ………………………………………………………………………………………………. ix SECTION 1. INTRODUCTION ……………………………………………………………………………………….. 1 2. LITERATURE REVIEW ……………………………………………………………………………… 3 2.1. COMPUTER SECURITY DECISION-MAKING …………………………………….. 3 2.2. SUSCEPTIBILITY TO COMPUTER SECURITY THREATS …………………… 4 2.3. FRAMING...
The Difficulty With Introducing Project Management Techniques in Digital Startups - The Difficulty With Introducing Project Management Techniques in Digital Startups
Table of Contents Introduction ……………………………………………………………………………………………………………………. 4 Problem Statement and Justification ………………………………………………………………………………….. 5 Literature Review ……………………………………………………………………………………………………………. 7 Proposed Solution Approach …………………………………………………………………………………………… 16 Results and Findings ……………………………………………………………………………………………………… 21 Conclusion ……………………………………………………………………………………………………………………. 28 References ……………………………………………………………………………………………………………………. 30
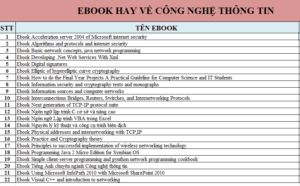
Ebook nghiên cứu về ngành Công nghệ thông tin - Ebook nghiên cứu về ngành Công nghệ thông tin
Ebook nghiên cứu về ngành Công nghệ thông tin